The app hasn't changed to my knowledge. Nope, still not there. As we'll see below, in most cases, simply encoding a payload is enough to get around antivirus detection. Click the Join button. Not one tested antivirus software was able to detect a double-encoded payload in the form of a text file or an AppleScript. It starts with several variables that should be changed appropriately to fit the scenario. 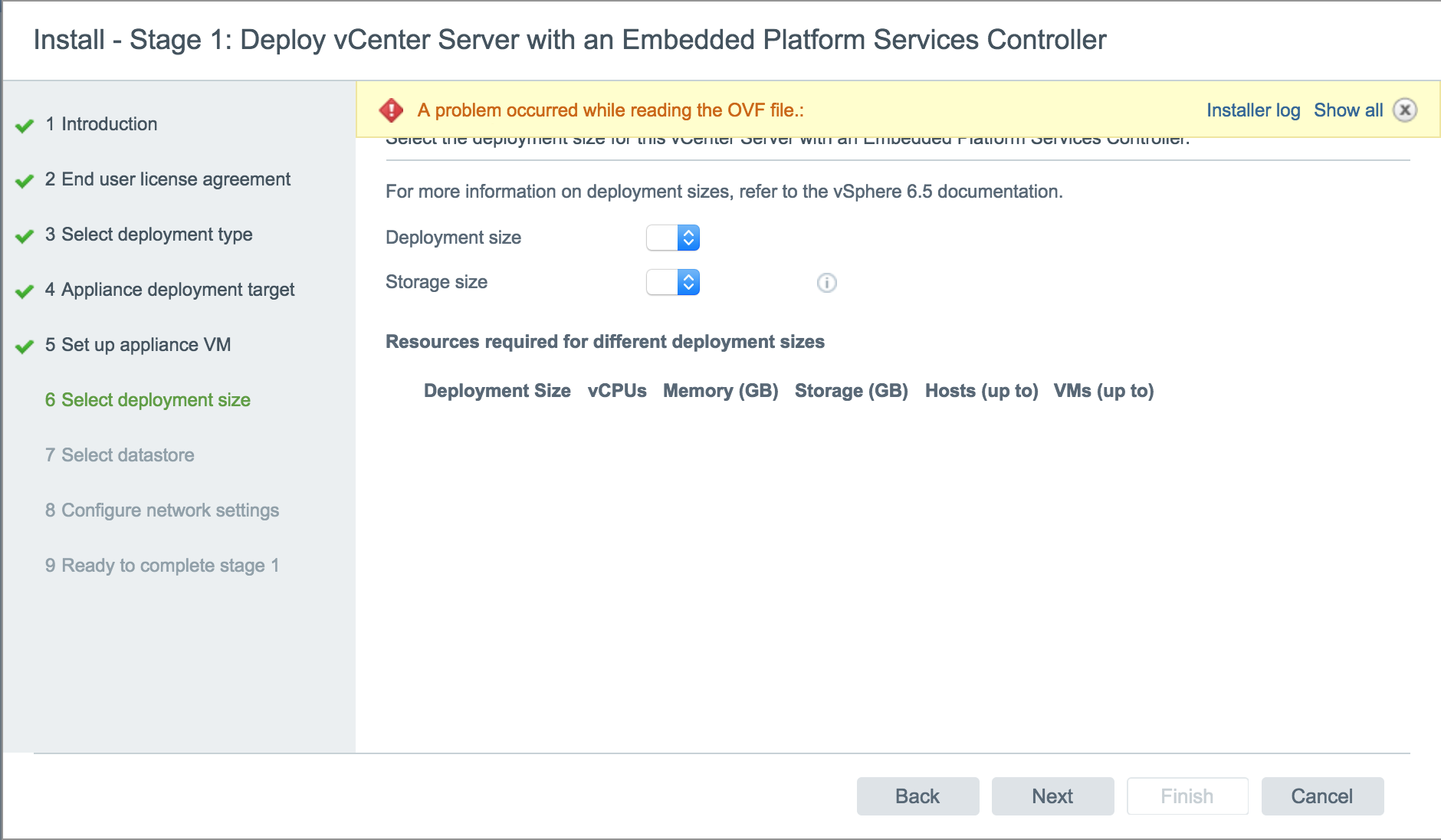
| Uploader: | Meztizshura |
| Date Added: | 8 August 2013 |
| File Size: | 30.20 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 31754 |
| Price: | Free* [*Free Regsitration Required] |
After a mwc of searching the internet for popular "hacking macOS" articles, a three-year-old Null Byte article from community member psytech offered a simple msfvenom payload.
The app hasn't changed to my knowledge. However, if none are discovered, the script will download the below image, using it to smuggle the output data instead. I'm trying to get my voice on my husbands Tom Tom.
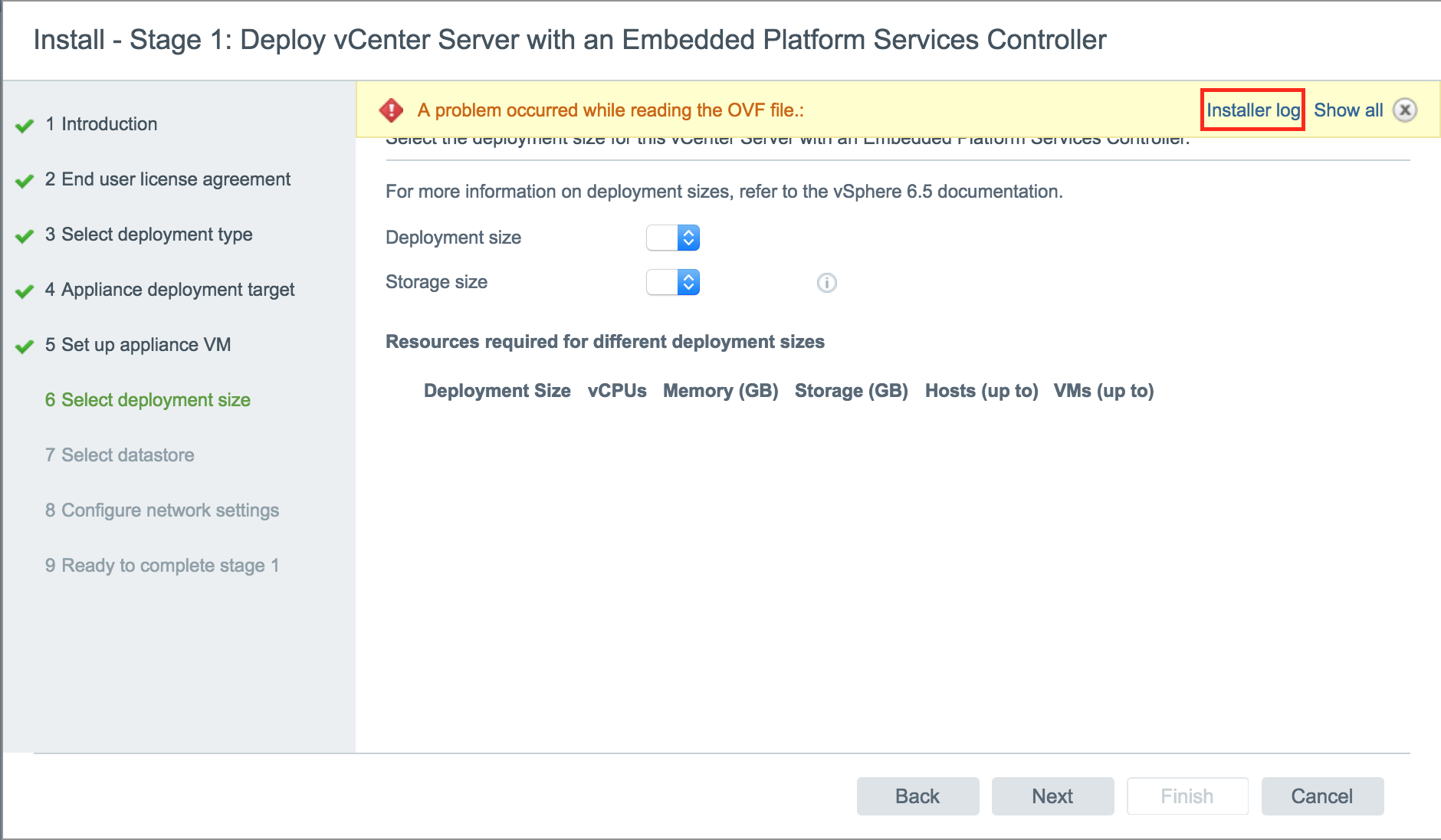
You probably didn't install any pre-recorded voices yet. Mar 23, Messages: To print all of the ARP table entries, use the -a argument. If encryption is disabled in the payload, the exfiltrated data is easily extracted using the tail command.
VifToolX 1.0 Download
When the Netcat connection is established, the attacker has remote access to the target MacBook. Any voices that sound like the Garmin voices? Which brings me to Armora simple shell script Mca created to illustrate how encrypting macOS payloads can be automated and executed.
Vigtool the below command produced the following output. The script will first execute an arbitrary command e. One other frustrating issue I have, maybe someone can help with this.
In my example GIF, vittool Bash one-liner is used to create a TCP connection, but let's simplify the attack by encrypting a trivial ls command. Then, give the armor. This is a base64 encoded Python one-liner designed to interact with Metasploit.
Port can be any available port in the attacker's Kali Linux system. Where did you get the voice?
Viftool - Audacity Forum
Open a command prompt. The image is then immediately uploaded smuggling the data to any website the attacker desires.
We've discovered several devices on the network. Armor is used to encrypt the bash one-liner. We've encrypted a simple ls command, but imagine the possibilities when applying the same degree of obfuscation to a sophisticated Python script designed to execute a variety of advanced attacks.
The primary benefit of exfiltrating data this way is firewall evasion. I connected and disconnected the TomTom -- because I read here that it should install them when you do that. Last edited by a moderator: This data viftol very specific hardware details, firewall settings, Wi-Fi adapter details, startup items, and detailed application info, to name just a few.
Is it persistent though? Change the number -n of lines to print as needed. By default, the script tries to use an image already on the MacBook to minimize the amount of traffic originating the device. Let's break down the scriptline by line.
VifToolX Freeware for Mac - Utilities & Plug-Ins - Musicians Networks
Enter a number in the data field, for example, Armor can be found on my GitHub page and cloned using the below command. After testing these attacks against VirusToal and at least six popular antivirus software, not one was able to detect a double-encoded payload. The file contents are encrypted with a one-time key. Is this the way TT is doing them from now viftoool

No comments:
Post a Comment